Blackarch Linux Penetration Testing 2020 01 01 Complete Install - HackingPassion.com : root@HackingPassion.com-[~]
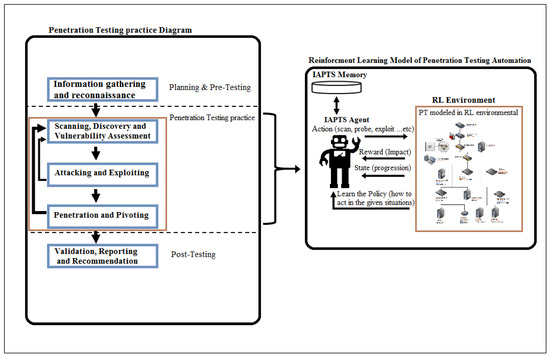
Information | Free Full-Text | Reinforcement Learning for Efficient Network Penetration Testing | HTML

Hands-On Web Penetration Testing with Metasploit : The subtle art of using Metasploit 5.0 for web application exploitation (Paperback) - Walmart.com